Computer Networks
ALL POSTS FROM CATEGORY
Remote Local Network Computer Management
It doesn t require installation and construction. Connects computers to different local networks, NAT. How AeroAdmin works. Details Remote access to the computer is the concept of remote connection to a computer via the Internet or a local network for the purpose of managing or reviewing a desk at a remote PK, as well as associated operations, such as the exchange…
Remote Computer Management In The Local Network
Run computers on your network remotely, free UltraVNC or Radmin, built in MyChat! The remote control program is your choice! Radmin or UltraVNC: you can choose a more normal one. If your network already uses Radmin, the choice is obvious. If remote control programmes are not yet available, we recommend the use of a free UltraVNC integrated in MyChat. Remote computer…
Computer Networks
MSK-IX speeds up communication between Internet companies by providing a neutral Internet eXchange platform for the exchange of IP traffic between networks and a DNS-server network to support root domain areas. More than 600 organizations use MSK-IX services to develop a network presence in key Russian telecommunications centres. MSK-IX includes communications…
Computer Network Concept
Knowledge • Basic methods, methods and means of obtaining, storing, refining information on the network; skills in local and global computer networks; knowledge of computer skills as a tool for managing online information. The ever-increasing amount of information in the world and the gradual editing of it on computers for compact storage have created a problem…
Global Computer Networks
Report by Marina Leonidovna Scuratov, Professor of Pedagogical Sciences, on the influence of television and the Internet on the development of children and adolescents. One feature of modern civilization is the transition to an information society, the rapid development of television and Internet technology. The presence of television in every house has led many…
Computer Networks For Kettles
Part I. First sign of computer Chapter 1. Don t be afraid of the computer. We ll get to know Chapter 3. Computer connection Chapter 4. Chapter 5. Windows Components Part II. Computer installation Chapter 6. System Block Magic Chapter 7. Head, ports and dips Chapter 8. Short-term storage: memory of Chapter 9. Long-term repository: discs and data carriers Chapter…
Local Network Computer Management
Applications for remote control of computers make useful and in many ways even fantastic things. For example, working in the office, but being physically on another continent. Helping a relative understand the complexities of the domestic PC by managing the process from another city. I m talking to my parents who can t even use a computer. Introducing, building…
How To Build A Network Between Computers
At the centre of the outer-screen window, a floating instrument panel is located, which contains a number of frequently used actions: the installation of the compound, the challenge of another mode, the selection of the current monitor, etc. This regime supports the Drag & Drop technology - the transfer of files and folders directly to the remote desk and…
Computer Networking
I DO Technologies engineers have implemented many computer networking projects. We have accumulated enormous experience in networking that helps us propose a precise and beneficial solution, depending on your demands. Choose an interesting option: ESTABLISHING SETI IN AFIS is the model decision for the establishment of a network in the office. The combined network…
Regional Computer Networks
The technologies for the construction of regional computer networks - Botic and Technology - Botic-Technology - are being developed by the Botic Telecom Laboratory, a joint laboratory of the Institute of Programme Systems of the Russian Academy of Sciences and the Russian Institute for Regional Research of the Federal Agency for Education of the Russian Federation…
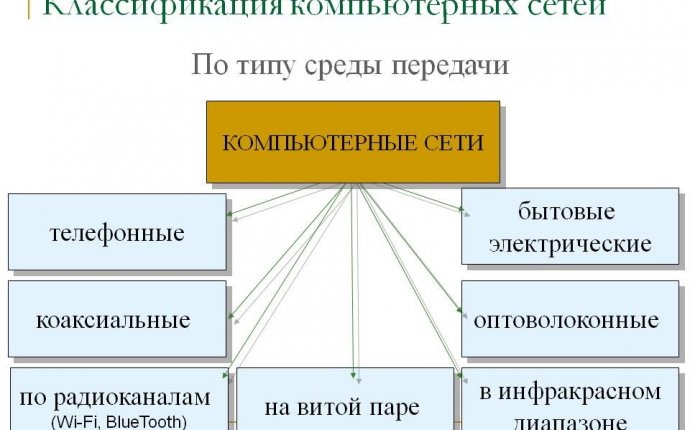
Classification Of Computer Networks
By way of organization, the network is divided into real and artificial. Artificial networks (pseudonets) enable computers to be linked together through a whale pair, and previously used successive or parallel ports, and do not need additional devices. Artificial networks are used when information needs to be downloaded from one computer to another. Real networks…
How To Put The Internet On A Computer
Do you have an iPad or a tablet on Android base? Turn him into a professional video surveillance system. Set annex Ivideon, and you will be able at any time to access the live video and archival videos of your cameras from anywhere in the world in a permanently high quality! To download the Ivideon Client on the smartphone, do you want access to the surveillance…